 10 August 2018
10 August 2018
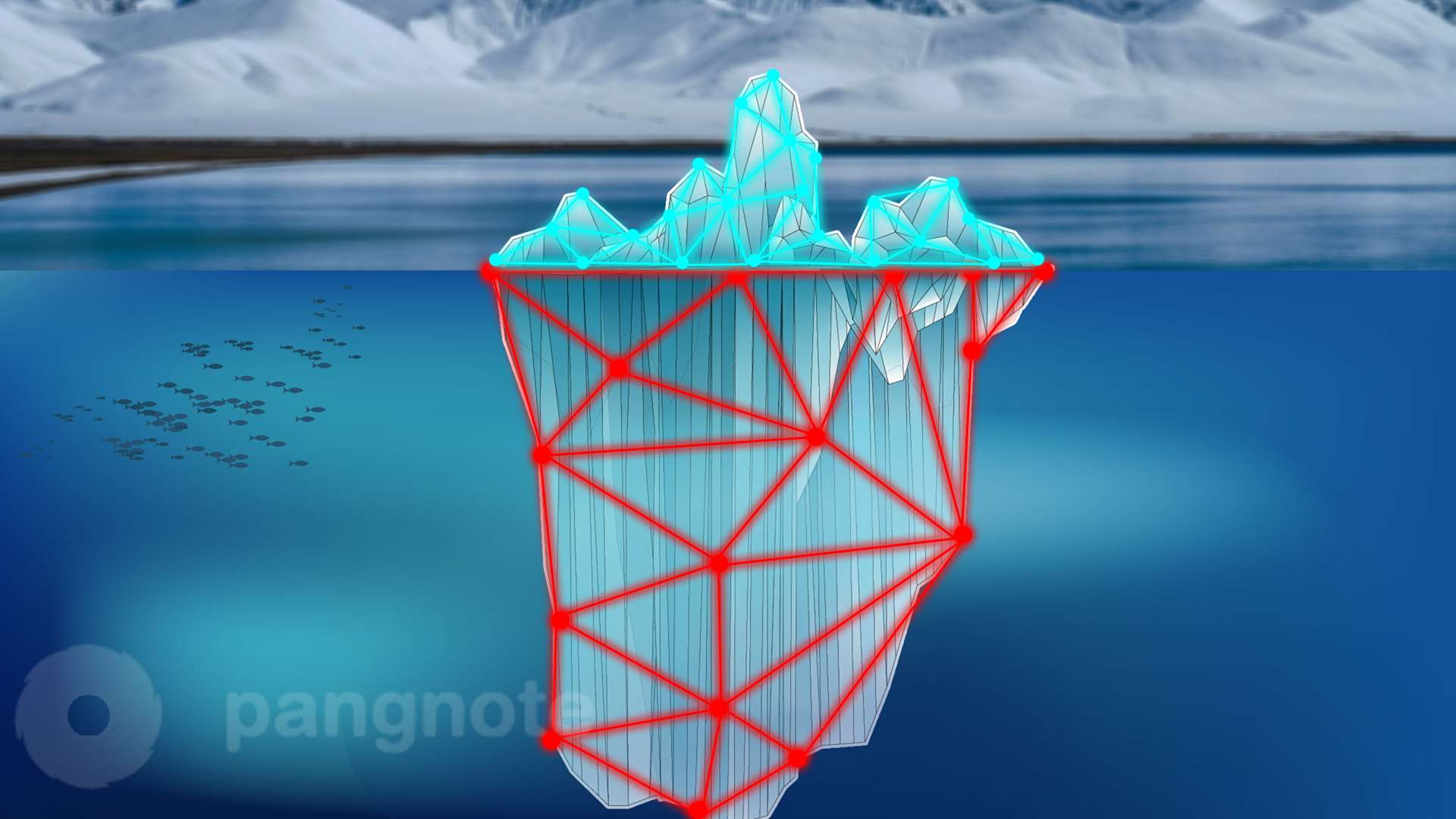
The IPv6 protocol provides as opportunities as well as risks
For many years, Internet users viewed the IPv6 protocol as a way to speed up network traffic and address the pending problem of the exhaustion of the network address pool. However, although many IT managers have controlled the development of this technology, and some organizations have already switched to this standard, still the most of enterprises that are not ready to solve new security problems arising from such a transition. Many companies seeking to migrate on IPv6, for example, every modern host server running Windows comes with enabled support for this protocol. At the same time, most IT departments have not yet developed a strategy and have not prepared their systems to adequately respond to possible problems. Many still use IPv4-based monitoring and security systems.
This allows attackers to install a fake IPv6 address over an existing IPv4 network and force clients to send information to the IPv6 network tunnel.
How does the threat act?
The new threat is based on the so-called Man-in-the-Middle attack. Dissatisfied employees can use this scheme to intercept Web traffic and track the actions of other employees of the company. In a more fatal scenario, they can modify or forge sites to organize an attack. In fact, an attacker can achieve his goal, having only the shell of the site. The purpose of such actions can be a phishing attack, an attack on customers and other ways of obtaining user registration data, as well as personal data, including credit card numbers.
Radical measures
The most radical way to completely eliminate the risk and eliminate any attack possibility is to completely disable IPv6. A more realistic approach for most enterprises is the combination of protective measures recommended by the Internet Engineering Task Force. For example, a threat can be minimized by segmenting and logically dividing internal networks.
In addition, now almost all Cisco switches now began to support RA Guard technology. If this technology is activated and correctly configured, the specified attack method will not work.
It is worthwhile to understand that all the listed methods are all just a bolt from the consequences of the global problem. The modern network infrastructure only begins its journey to the transition and implementation of IPv6. Only the general use of this protocol can forget about the threats of implementation.
0
0
Comments
How do changes in the structure of world traffic affect the DC?
18 December 2018What is safer to use in the DC: hypervisor or containers?
3 August 2018Top 5 Data Center Trends for 2020-2025
2 October 2020Recommendations for data storage using a dedicated server
9 March 2019Let`s talk about free domain hosting
10 November 20195 life hacks for more efficient SQL work
24 January 2020What is PTR? How is PTR different from DNS?
19 August 2020Prospects for improving the reliability of flash memory for SSD
22 September 2020How likely is it that your site will "fall" during the holidays?
5 June 2018How to deliver growing data from the end user to the DC?
25 January 2019VPS server uses for development and testing
22 May 2019Why it is worth to buy VPN and not trust free service
18 September 2019Three backup strategies for data protection
8 July 2019Getting offshore dedicated server for rent
6 April 2019What is freeVPN connection and how to use it?
27 August 2019Computable IT: Betting on a software approach
19 December 2019How and for what tasks choose a dedicated gpu server?
23 March 2019Machine learning in the data center
8 October 2020How to choose RAID for dedicated servers hosting
9 March 2019The new Cisco SD WAN is the ideal solution for the corporate network
4 August 2018Readiness of employees for digital transformation in the company
23 July 2018From the cloud to Edge Computing and vice versa
9 March 2020Key benefits of setting up web host dedicated server
6 April 2019A new player on the x86 processor market
4 August 2018The technical nuances when buying a cheap VPS servers
11 May 2019Tips how to work with cloud server backup
13 June 2019New IBM FlashSystem 840 allows to store in rack up to petabyte
16 May 2018Intel will introduce a new processor architecture every 5 years
2 March 2020Technical view: how resources are transferring on the Internet
17 November 2019Why computer chips started to wear out faster?
3 July 2018When should I choose a cloud file server?
10 June 2019Roadmaps to a Single Socket Server Future
16 December 2019Why Intel is returning to 22-nm process technology
11 October 2018How to use VPN on own virtual server?
20 September 2019Cloud Security Issues and Solutions
26 December 2019Why do large IT companies lay own underwater cables
3 August 2018How to monitor the work of the business process
4 August 2018AMD vs Intel: core race
3 July 2018Features of choosing Windows dedicated server
23 March 20195G Technology: New Opportunities and New Challenges
14 November 2019Modular data centers: to whom, why and how?
29 May 2018How realistic is it to buy dedicated server with a low fees?
6 April 2019Intel promises to expand production to meet the demand of the CPU market
3 October 2018Cases of accidents in DCs in 2021
31 August 2021How Cisco sees the future development of IBN technology?
5 January 2019Robotic integration in data centers in 2021: cases and forecasts
30 July 2021Google begins development of its own Systems on Chip to reduce power consumption of large-scale comp..
11 May 2021How does cloud station server infrastructure works?
17 June 2019Cases when VPS is not the best solution
23 December 2019Reasons for hosters to buy IPv4 address space now
1 March 2019Scenarios of edge computing future
12 July 2018Fujitsu and Huawei entering the market of AI processors
5 July 20183D printing will be used for CPU cooling instead of thermal paste
8 December 2018The future of offline computing in data centers
17 September 2018What for was Pangnote created for?
14 August 2018Market prices for IPv4 ranges in 2018
23 May 2018Backup technologies that are used on the server
5 July 2019Configuring VPS file server Operation
11 May 2019Dedicated servers against clouds: when it is better to use
27 September 2018Options for the strategic planning of IT infrastructure deployment
23 September 2018Mass attack on sites with the WordPress engine
1 October 2018The global market for commercial cloud equipment is tend to grew by a third
12 July 2018100 Tb HDD will appear on the market by 2025
10 November 2018What is VPN service and who is using it?
4 November 2019US government will crash IPv4 market
22 June 2020The development of quantum computers surpasses existing information security technologies
15 April 2020Thinking of buying IP addresses? Reasons to do it
8 September 2018Serious transfer issues from IPv4 to IPv6
18 November 2019What changes await the clouds in 2020
20 February 2020New drives for data centers: Toshiba introduced the SSD, and Seagate has released the HDD
4 October 2018The growing complexity of personal cloud server as a new information security issue
26 May 2019IT giant leaves the chips market for DC
23 January 2019Why hosters set limits even for top VPS server
20 April 2019Using blockchain in banking and trading
7 November 2019NVMe over Fabrics: new storage technology
3 August 2018What is better to choose from domain name suggestions
8 November 2019What is the guarantee of effective cloud infrastructure
10 August 20185G will transform cheap cloud server services and their work model
9 June 2019How to improve the efficiency of DC in the process of operation
9 February 2019Intel is launching a 48-core processor for Xeon Cascade Lake-AP family
6 November 2018How provider can help company with disaster recovery
25 August 2018Why IP rental price is constantly growing?
9 September 2018Why it is worth to buy VPN and not trust free service
5 October 2019What is the traceroute command used for and what does it show?
31 July 2020Forecasts for DC server market for Q3-Q4 of 2018.
21 September 2018Is it possible to get 100% anonymous VPN?
31 October 2019In 2019, more than 65% of enterprises will have a digital transformation strategy
3 August 2018The cost of IPv4 addresses almost doubled in 3 quarters
26 July 2021New solution from Huawei: AI-processors for data centers
16 October 2018All you want to ask about IP sell process
1 September 2018Data Center Technologies for Video Production
26 September 2018In the market of cloud services, the leaders are hyper scalable solutions
27 September 2018How will the new billion of users affect the development of the Internet?
28 September 2018DNA storage technology: the future or failure projects?
26 August 2021Using a Wi-Fi VPN does not allow you to reliably protect a public network
1 October 2019Hosting for a startup: shared, cloud or own server?
4 July 2018New family of SSD from Micron company with up to 7.68 TB capacity
19 January 2019The launch of quantum networks has become even closer
25 February 2019Multi Actuator technology allows you to double the performance of HDD
4 August 20185G technology has security protocol weaknesses
22 November 2018Why do SSL connection errors occur and how to fix them?
24 December 2019Lenovo presented equipment for DCs
9 July 2018Is it worth to buy domain at the highest price
3 November 2019What to do if Linux dedicated server under DDOS attack?
30 March 2019Cockatoos threaten the development of a nationwide network infrastructure in Australia
5 June 2018The DNS server is not responding. Check your IP address settings
1 May 2020Samsung launched mass production of corporate 30TB SSD
6 June 2018Which country is best to look for a bulletproof hosting
22 December 2019How to buy or sell your RIPE IPs with the best price
4 September 2018How to avoid mistakes when choosing a hosting
17 September 2018Tips for keeping your infrastructure working during Black Friday week
20 November 2018Checklist: what to look for when choosing a dedicated server hosting
9 March 2019Nanoservices come instead of microservices: why and where are they needed
16 April 2021Delta Electronics has demonstrated how to build "green" data centers
1 November 2018US decides to abandon US and Hong Kong cable stretch due to possible cyber espionage from China
22 July 2020The DDR5 standard is likely to be only in 2019
25 August 2018Sale of IPv4: from agreement till receipt of payment
8 September 2018Trends of data storage in 2018
29 May 2018What are the special issues and what is the dedicated server definition?
6 April 2019Use, configure and rackspace dedicated server
13 April 2019The biggest semiconductor manufacturing plant will be opened in Korea
22 December 2018How GDPR caused the leakage of personal data
1 January 2020General Domain Transfer Rules
21 February 2020Types of VPN for secured Internet connection
9 September 2019Replacing lithium: new battery technologies
26 December 2018What problems does blockchain pose to companies
6 November 2019How DCs use unique technical solutions to provide cheapest dedicated servers
9 March 2019How do DCs of the world market of colocation leader work
21 September 2018How to found out does your VPN online server save the logs?
28 August 2019Do you know why we need data centers?
7 December 2018The procedure of purchasing web domains
7 November 2019Norwegian government wants to make Norway the world leader in hosting services
30 May 2018DNS over HTTPS was approved but not everyone is satisfied with it
17 November 2018How to reduce server response
28 June 2020Fujitsu and Huawei are developing AI processors
19 January 2019Why is server rental in England is considered to be an exceptionally good idea?
6 April 2019The work of data centers has become less reliable
23 September 2018How to understand what do you need Proxy or VPN?
23 July 2019Features of VPS server hosting as a product
20 April 2019How multifactor authentication looks like in the DC?
1 June 2018How to reduce costs on the enterprise cloud server?
23 May 2019Facebook builds its own optical backbone across US to minimize ping
5 May 2021How to get secure VPS server if you are renting it for the first time
18 May 2019Obstacles encountered in the blockchain implementation strategy
8 November 2019VPN unlimited myths and why this service should be used?
25 July 2019AMD and Xilinx created a system with record performance for AI
27 February 2019Silicon photonics technology are coming to DCs
9 February 2019Synology RackStation presented 1U Rack Storage
8 December 2018Backup as one of the most important elements in the operation of any project
11 July 2019Unbelievable Power Usage Effectiveness of underground Iron Mountain DC
21 May 2018New OpenStack Rocky works on bare metal without server OS
13 September 2018Domain Life Cycle
25 June 2020The main vectors of enterprise cyber attacks on in 2019
16 February 2019The multi-cloud future of data centers
18 July 2018What you should ask for when looking for Windows dedicated servers?
16 March 2019Samsung plans to become one of the telecommunications equipment manufacturers leaders
27 September 2018Technologies for building the Internet of the future are presented by Cisco
29 January 2020RIPE NCC will now allocate only return blocks
31 December 2019The future of IP allocation
13 February 2020What is now more popular in the market for containers or virtualization?
16 February 2019How the spread of 5G will affect the development of PCs and mobile devices
25 December 2018ICANN again raised the issue of lifelong domain registration
10 December 2018How to rent IP addresses
4 September 2018What should you know using the VPN access
16 October 2019How to choose the best dedicated server hosting cheapest ?
16 March 2019How to decide on the concept and decide whether you need a openVPN?
27 August 2019How does it work and VPN comparison VPN with proxy and Tor
4 November 2019Key principles and development steps of the Landing page
13 February 2020What is a site backup and how to create it?
23 July 2019Growth and transformation of local data centers in competition with the cloud
22 September 2020How GDPR affects the international hosting market?
27 May 2018Iridium and Amazon are planning to create global satellite internet for IoT
11 October 2018How to become LIR in 7 days
30 August 2018Lithium-ion batteries as UPS in the data center
17 August 2018Water cooling in the data centers: reasons of popularity
17 July 2018Scenarios for network development in the face of a lack of IPv4 resources
17 November 2019What to expect if you decided not to use SSL?
14 November 2018How IaaS provider organizes information security
4 August 2018How to ensure the operation of outdated systems in DC?
7 December 2018Should providers develop cloud services?
13 December 2019Who is FinOps and why is he needed when working with a server cloud?
21 June 2019In 2020 AMD will present processors with a new Zen 3 architecture and 7nm + technology
17 November 2018Gigabyte video card with GDDR5X memory
3 November 2018Advantageous IPv4 rental in details
8 September 2018Big sales for e-commerce is challenge for hosting
10 August 2018What can become a reason of high load on Germany VPS server
11 May 2019Data center strategy to protect against cyber attacks given the trend of their growth
26 August 2018What DC should expect from data sphere by 2025?
16 February 2019What technologies will determine the future of DC
1 December 2018Business is placing digital counterpart of company’s equipment in external DCs
22 July 2018Why IPv4 rent is extremely popular lately?
30 August 20183 technologies capable to change the hosting industry
19 January 2019Cybersecurity trends in 2019: from mobile devices and IoT to cloud
17 December 2018Features of VPN configuration technology
3 November 2019Cloud helps cope with IP blocking
13 December 2018Covid-19 will become a factor in the transformation of business and IT sector
5 May 2020What is more important for the domain name length or readability?
21 September 2018Why smart IaaS provider does not build its own data center?
4 July 2018Business readiness to rethink way of working with big data
22 July 2018Features of hosting industry in Lithuania
17 September 2018The idea of the best dedicated server for each user is different
30 March 2019ASUS reported record server performance
2 March 2019Networking Trends for 2021 from Cisco
10 February 2021New faster and more stable data-storage for data centers
3 July 2018General VPN Linux setup issues
7 October 2019How to significantly reduce cloud costs?
30 March 2020Cloud SQL server hosting and its features
20 June 2019Citrix Systems preparing new infrastructure solutions
11 August 2018Problems of choosing between IPv4 and IPv6
24 November 2018Corporate data centers will be replaced by commercial ones
4 August 2018Intel's new Core-X processors: 18 cores at 4.5 GHz
11 October 2018Can blind spots be avoided when monitoring DCs?
3 November 2021Hewlett Packard Enterprise presented solutions for hybrid cloud environment
14 September 2018New tape storage systems for data centers
22 October 2018Storing secure data when using a server cloud hosting
27 May 2019How did domain names appeared and why?
4 November 2019Modern trend in technical support in data centers
14 January 2021What is VPS and usage tips?
13 April 2019The IPv6 protocol provides as opportunities as well as risks
10 August 2018Is it true that hosting is important for SEO of your site?
31 May 2018Norway will oblige data centers to use the generated heat in public needs
8 April 2021The blockchain market is growing: where, how much and how data centers should act
22 August 2018New Asus motherboard with the possibility of extreme overclocking
30 October 2018Tips for managing server infrastructure
4 August 2018Why dedicated server hostings centers are interested in UL 3223 certificate?
9 March 2019How is the cost of hosting in the data center formed
14 November 2019Feedback. Why should I suggest on how to improve the Pangnote resource?
18 August 2018Why IP addresses are in demand and how to switch to IPv6?
13 November 2019AI systems optimize the cooling of servers in DC
13 September 2018Global information security threats: trends of 2018
9 June 2018New IBM Power9 servers with machine learning processors
3 July 2018Seagate and IBM are planning to create HDD blockchain-tracking system
12 November 2018Intel presented fresh research and solutions for smart factory
22 May 2018ICANN Chair sells 14 Million IPv4 and Creates APNIC trust fund
16 June 2020Benefits of using file server in the cloud
28 May 2019Using Multiple Domains: what you should know
31 May 2018Edge computing server selection algorithm
1 June 2020The Excellence Data Architecture Design Award is given to Datacenter.com
11 May 2018Backup hardware storage performance for back-up
4 July 2019How to copy a site to my domain?
9 November 2019The way to increase DC fault tolerance lies through minimizing the human factor
15 December 2020Who should NOT move into the cloud and why?
6 July 2018What are the real advantages of using blockchain in an enterprise in 2020?
24 April 2020Supermicro released Platform with 320 PCI Express buses
2 December 2018Google is building 5 new data centers in the USA for Google Cloud platform
23 May 2018How hosters do the pricing for cheap dedicated server hosting?
23 March 2019What will be ICANN's response to the domain prices' rise in .COM zone?
27 November 2018Lenovo DS6200 storage functionality
4 August 2018How to protect your domain name and web address?
3 November 2019Kaspersky Lab is building a data center in Switzerland
9 June 2018China has developed and launched its own server processors manufacturing
10 April 2020Give me two: why do you need twin domains
6 July 2020Principles and frequency of backups to the cloud
3 July 2019Cisco is working on the implementation of the Intent-Based Networks concept
8 November 2018Data availability increasing level and security as a trend or a necessity
14 February 2021How AI can help network administrators
3 August 2018US government will oblige global providers to tighten control over submarine internet cables
20 November 2020The feasibility of internal data centers is beyond doubt even in 2020
14 January 2021Will users be able to get kinetic infrastructure soon?
17 April 2020Prospects for Data Center Transition from Diesel Generators to Hydrogen Fuel Cells
22 March 2021VPN service free: there is a catch
11 October 2019Methods of rising the efficiency of data centers
17 July 2021What will telecommunications companies face in 2019
23 February 2019The world's first hybrid x86-compatible architecture has been released
15 December 2018The use of new generation DCIM solutions in the data center
17 July 2018How should modern backup solution looks like?
22 November 2018How to find and fix 404 errors on your website
14 January 2021Colocation for small / medium business
21 September 2018Apple introduces a 1-year SSL limit for Safari
28 November 2020HDD market will shrink by a third by 2021
19 January 2019How to transfer site to https without loss of traffic
29 December 2019Risk Management and Scalability of FTP Cloud Server
1 July 2019How to choose and buy VPS server USA?
25 May 2019What problems will the VPN provider face?
21 September 2018The useage of edge computing in the industrial sector
3 February 2020What IP broker can do for you?
3 September 2018Why use a VPN and how to get secured internet connection?
20 October 2019Protecting your site from DDoS attacks, hacking, spam and viruses
26 January 2020DRAM memory price started to decline: forecasts for 2019
9 November 2018The number of users using IPv6 to connect Google servers has reached 25%
22 October 2018How to reduce operating costs in data center
30 May 2018Cloud Saas technology and customized server
28 May 2019How to transfer infrastructure to the cloud and choose cloud server providers?
15 June 2019New energy-efficient trend: DC in windmills
5 January 2019What questions about IPv6 implementation should you ask yourself?
16 November 2019Cloud virtual cloud servers is a technology superior to all other types of hosting
12 June 2019Why it is better to use Linux for cloud computing
11 June 2019What IPv4 broker do and how to transfer subnet?
2 March 2019How to calculate and what determines the load on the dedicated host servers?
23 March 2019Data centers construction trends
23 July 2018The frequency of accidents in DC has decreased and the sum of damage has increased significantly
26 October 2021Hosting reseller: how to find a reliable one and why is it more profitable for a user?
15 December 2019Domain lookup system and how use it
16 November 2019Pangnote is buying your IT stories
22 June 2019Five Top Issues After Migrating to the Cloud
13 February 2020The new Intel Core 9th will support up to 128 GB of RAM
22 October 2018Eternal hosting: how is this possible and the features of the service
30 April 2021What to do if the webpage takes a long time to load?
17 November 2019UK is planning to provide warship to protect submarine internet cables
19 April 2021IPv6 and IPv4: which is better?
12 November 2019Choosing a VPS servers for your project and where to find it
13 April 2019Search of Dedicated Servers using the Pangnote
15 August 2018Dell company has started 2018 by expanding its PoweerEdge server
18 May 2018Consider the example of Microsoft Azure how quarantine has affected data center congestion and traff..
14 July 2020Choose the best way of cloud migration
4 August 2018VIA will help the Chinese company with the production of its own processors
19 December 2018How to design page 404 to attract users?
19 April 202012-bay rackmount NAS server from Synology RackStation
6 November 2018How RIRs offer to solve the problem with the lack of IPv4 addresses
10 August 2018The failure of the cloud: how to react
11 August 2018The USA is the most reliable country for building data center
21 September 2018Threadripper 2: 32-core desktop processor from AMD
7 June 2018Super VPN is perfect solution for inter-branch communication
15 August 2019Russia started mass production of Elbrus-804 servers
22 October 2018Places on the planet where the use of the Internet is a real challenge
26 September 2018How to set up a mail server so that the message does not get into spam
22 March 2020Microsoft successfully loaded the data center into the North Sea
7 June 2018Global information security threats: trends of 2018
5 July 2018Two thirds of cyber attacks are purposeful
13 February 2020How to achieve 100% of the project's availability?
25 July 2018The main problems in the field of automation in 2020
27 January 2020One more time: how dedicated server differs cloud
21 May 2018Why IT costs are growing and how to reduce it
6 August 2018Influence of automation in DC on engineering personnel
30 October 2021Domain registrars refuse to disclose WHOIS data even for trademarks protection
2 November 2018What is the status and future of the satellite Internet market?
31 December 2018Proxmox tools for performing data backup
9 July 2019Features of VPS Ubuntu server with a test period
20 April 2019Why and how to buy drop domains?
10 July 2021Searching of virtual and cloud servers using the Pangnote
15 August 2018The Chinese are developing an underwater data center
7 July 2021IPv4 Lack and NAT Technology
23 November 2019ICANN News: new WHOIS Reform
13 September 2018Features of smart PDU in data centers
3 November 2018New AMD processor will not require software optimization
2 February 2019The cost of IPv6 implementation and who does actually need it
25 August 2018Information security based on the use of VPN service
2 September 2019Indian provider laid trunk cables to Singapore and Italy
24 June 2021What is the reason for the global increase in the number of hyper scalable data centers?
15 November 2018File server cloud: economy and safety
7 June 2019Introduction into domain info, elements and concepts
6 November 2019Rules How to try to protect your personal data online?
30 January 2020Technologies waiting for growth boom in 2020
12 April 2020Facebook improves connectivity in the African region with an undersea internet cable
7 November 2021Tips about how to buy IP addresses
3 September 20185 directions of IoT development
25 July 2018Gaps in load distribution between DСs in China carries the risk to the country's infrastructure
29 November 2018Network connectivity issues become the leading cause of data center downtimes
13 July 2021Diesel free and green backup of power grid in DC
20 March 2020The processors`s market In Germany led by AMD
7 November 20184 virtualization trends in 2019
2 February 2019Big Data: changes in 2018
6 July 2018Basic principles for setup of VPN server
26 September 2019Serverless computing, multi-clouds and automation of IT infrastructure as trends in virtualization
3 August 2018In what way does cloud hardware matter?
2 February 2019What is a domain name and how to use it?
15 November 2019Infrastructure Migration to the Cloud: Problems and Experience
16 October 2018The information security industry is growing thanks to cyber attacks
25 July 20185 reasons to test and get VPN trial
2 November 2019Pangnote something like a hosting marketplace
11 May 2019How to buy IPv4 subnet with minimum risk and optimal price
6 September 2018More than two thirds of enterprises have problems with PoE solutions
3 July 2020Tips to guide the data centers in 2018
26 August 2018What slows down the implementation of IPv6? Is it worth implementing this protocol?
24 November 2019Common Shared Hosting Issues
11 November 2019Creating GPU-based systems for the clouds
14 December 2019Cloud equipment production volume show strong growing trend
19 January 2019AFRINIC can return a large pool of addresses that were assigned by their employee
31 January 2020How to choose the VPS Linux server
20 May 2019New cyber threats in the global network and VPN unblocker
16 September 2019How and why does China invest in the infrastructure of the Internet
4 June 2018Why you should not use VPN for Mac everyday
13 September 2019Reuse trends in data centers
5 June 2020Tips on how to avoid problems with the creation and recovery of backup
22 August 2018How does it work and VPN comparison VPN with proxy and Thor?
28 October 2019The global cloud services market contributes to the emergence of new business models
9 February 2019Dual-Mode Enterprise SSD Controller from Silicon Motion
2 February 2019Cooling of DC: sources, tools, solutions
9 July 2018Intel is redesigning its processors without Meltdown & Spectre
25 May 20183 levels of domains name management
15 November 2019How DC use programmable microchips for clouds
23 February 2019Decided to IPv4 sell? Ask us how!
29 August 2018What to expect from GDPR 2.0?
11 December 2018Data center spending trends in 2020
15 March 2020How the growing popularity of the Internet of things affects the data centers?
27 May 2018Cisco is developing a hyperconvergent ecosystem
1 October 2018What you need to pay attention to when setteling agreement with a domain registrar
16 November 2020The necessity and logic of the backup process
22 July 2019What Webmasters Need to know about domain name server
5 November 2019IP Broker: how can he help your business?
9 September 2018How to prevent getting the IP address in the blacklist?
12 November 2019Data Centers are preparing to help with digital transformation
14 September 2018How dangerous are tracking cookies if you really have nothing to hide?
4 January 2020Cisco C480ML M5 server for working with AI
21 September 2018Will 2020 be a watershed year for IoT?
6 February 2020What to choose for online store: Unique design or template?
5 January 2020Let`s take a look on a blade server and who benefits from using it?
21 December 2019Process of domain check and its evaluation
21 November 2019About data storage trends in 2019
26 January 2019Cloud DRaaS as a cloud-based server disaster recovery service
13 September 2018Search tool for the purchase or sale of IP resources on the Pangnote platform
16 August 2018What problems can you face if you need to buy ipv4 space?
2 March 2019What to look in SLA when choosing server cloud backup?
18 June 2019How to protect the domain from theft?
2 April 2020Tips for setting up cheapest dedicated server
11 March 2019FTP connection errors and their solutions
5 April 2021Automation of processes for business
3 August 2018How the hosting for a modern site should looks like?
25 December 2019Huawei modular data centers allow to save up to 40% on construction stage
29 December 2018Exhaustion of ipv4 addresses in AFRINIC region
16 May 2018What is VPN and why it is the maximum protection and convenience
14 August 2019European cloud providers can hardly compete with the American
28 March 2021VPN software for setting up a private network
23 September 2019How does migration to the cloud happen?
27 December 2019Storage systems configuration on dedicated server for rent
30 March 2019Emoji-domains - the future of the Internet?
6 June 2018From September 2020 Google introduces a 100% mobile-first serch results
11 May 2020What should the client look for in the data center?
21 September 2018Searching for a colocation using Pangnote
16 August 2018HPE on the corporate blockchain market
19 January 2019The choice of VPS location directly affects the response time of the site
11 May 2019How to buy IPv6 address?
6 September 2018Facebook is planning to invest 1B $ in expanding "green" data center
22 May 2018How to make a corporate DNS secured and failover?
19 January 2019How to combine HCI with your existing IT infrastructure
18 December 2019Cheapest VPS Management Technologies
20 April 2019Certification of modular data centers
28 September 2018Advantages and disadvantages of using FreeBSD dedicated server
30 March 2019New storage solutions from Fujitsu ETERNUS
30 May 2018E8 Storage system shows minimal latency and high potential of NVMe
8 January 2019Site big database hosted on good VPS servers
11 May 2019AMD EPYC's success forced Intel to sell Xeon cheaper
2 October 2018Mobile versions of sites will replace mobile applications in the future
13 February 2020Transformation strategy of telecom operators to cloud server providers
8 June 2019ICANN works to recognizing internationalized names in China process
19 January 2019Features of domain name system in the US
10 November 2019Search for IP transit and similar specific services using Pangnote
17 August 2018Huawei has presented Enterprise Infrastructure News
27 February 2019Using graphics processors to protect against virus attacks
18 July 2018Experts doubt in the need of transition to IPv6 until 2023
29 December 2018Popular types of virtualization for rent VPS server
17 May 2019Problems of microservices caused by a lack of understanding of the basics of technology
9 February 2019Guarantee of best dedicated server hosting depends on the data center
23 March 2019Choosing between IPsec and site to site VPN technologies
26 October 2019In October AMD will present new graphics processor the successor of Radeon RX 570
11 October 2018The Chinese company will enter the market of x86-processor manufacturers
17 July 2018Tier certification for DC: the pros and cons
11 August 2018The Telegram blockage dramatically increased the demand for VPN services in data centers
25 May 2018Main fallacies when comparing your own servers with the cloud
10 July 2018Cloud vs NAS: the main differences between backup technologies
2 July 2019Height of cabinets in the data center is growing
28 November 2018What is happening with expired domains
20 November 2019IPPON has updated its on-line UPS line for data center infrastructure
30 October 2018How it works and why to use S3 Object Storage
27 December 2019Backup as a guarantee of protection against ransomware viruses
10 July 2019What you first need to take care if you decide to rent a managed dedicated servers?
13 April 2019Choosing VPS or dedicated server hosting
19 May 2019Differences between cheap VPS server and shared hosting
20 April 2019Serverless computing on the way or how will the clouds change in 2020?
5 April 2020New SD-WAN and Updates for Cisco SDA and Cisco ACI
26 October 2018What determines domain name value and what is subdomain?
9 November 2019Europe's data center market will see the biggest growth in 2020
22 September 2020IP lease and maintenance of autonomous systems AS
1 September 2018What is HPE focused on and what innovations to expect
2 February 2019Strategies for moving companies to the cloud
9 February 2019Tips how to get best VPN service
5 September 2019World colocation market will continue to grow
13 September 2018Community based organizations require ICANN to supplement domain use requirements
13 February 2020Little less conversation, little more actions. How Pangnote plans to reduce the time it takes to fin..
18 August 2018How to choose web domain name?
11 November 2019What are other standards for evaluating data centers other than TIER?
11 December 2019Cooling system for data centers from Schneider Electric
29 October 2018Do you need to speed up your website?
26 September 2018Cyrillic domain name registration: pros, cons, pitfalls
9 November 2019What to do if IPv4 is blacklisted?
18 May 2020Looking where to buy IPv4 addresses?
30 August 2018Google and Facebook abandoned part of the submarine cable due to trade wars
27 February 2020Which SSL to Choose for a Website: Paid or Free?
18 March 2021How to effectively use the free test VPS server
21 May 2019What is the difference between a virtual server and a dedicated server cheap?
13 April 2019APNIC members begin a forced transition to IPv6 because of IPv4 Exhaustion
22 November 2019To create a global network it is proposed to use space lasers
25 January 2019Three Phase HSTP UPS Series from CyberPower
29 October 2018SSD based on 64-layer 3D NAND developed by Intel and Micron
19 January 2019UN published transition plan for Ipv6
10 July 2018News of the cooling systems market for data centers
29 May 2018Why does big data need an opensource cloud server?
19 June 2019Barriers of the business in digital transformation
6 August 2018Recommendations for choosing a domain name and domain zone
19 November 2019VMware Empower Can Change the Future of Networking and Virtualization
12 December 2019DARPA Creates New Networking Approaches to Increase Distributed Application Performance in 100 times
17 December 2019Choosing a CMS for online store
20 November 2018Cisco is confident in their way of innovation
24 May 2018Do You want to get IPv4 lease?
30 August 2018What determines the fault tolerance of dedicated server cheapest and how to check it?
30 March 2019What CIO need to know about the technical side of omnichannel connection
26 August 2018The rise in popularity of IPv6 has not caught up with the size of the critical mass to concur with I..
4 September 2021Software is going into the cloud
23 July 2018Is your organization ready to provide security for hosting cloud server?
14 June 2019Why Pangnote a roaring Hosting services exchange and does not look like a forum
14 August 2018Pillars of E-commerce hosting: high speed and up-time
18 May 2018IPv4 blocks rental: prices and conditions
9 September 2018The advantages of serverless computing do not compensate for their disadvantages. Understanding why
12 October 2020Chinese manufacturer Loongson will enter the market with 16-core processor in 2020
11 October 2018The server market news: x86 is still growing, mainframes are falling harshly
21 August 2018IaaS Market Trends
4 June 2018Losses and the number of cyber attacks on the companies are constantly growing
16 February 2019How do colocation providers protect clients data?
28 December 2019The increased number of new devices stimulates the usage of IPv6
23 July 2018What data centers do to offer cheap dedicated server?
9 March 2019Google abandons free Wi-Fi project worldwide
12 March 2020The fight of ISP against illegal use of IPv4 using BGP
10 June 2020What you need to pay attention to when choosing a colocation provider
2 February 2019Seven digital shocks that making CIO difficulties
20 December 2019IPv4 buy solutions from official broker. Trading platform Pangnote
29 August 2018Google’s TPU 3.0 Machine Hardware Accelerates and Becomes Faster
11 May 2018Hivelocity presents instantly deployable dedicated servers based on AMD EPYC
25 May 2018Quantum computer race is started
17 July 2018Choosing webhosting platform: Unix or Windows
21 November 2019The role of technical support in the work of the cloud servers providers
16 June 2019AI and its development become the key to the success of cyber attacks
24 November 2020What is an IP address and why is it needed?
13 November 2019New trend: companies are choosing cloud server in own infrastructure
24 May 2019Common mistakes that companies make when deciding to create a site
3 January 2020Why not choose a free VPN service free?
24 July 2019Use monitoring service for early detection of DDOS attacks
4 June 2018Features of Chinese Hosting
13 August 2018Backbone operator Telia Carrier became the property of financial funds
9 December 2020The RAM for the data centers will become cheaper
2 October 2018DCs should prepare for new storage infrastructure solutions
4 August 2018Current Status and Future for Implementing IPv6
22 November 2019Chinese IT manufacturer introduced its own NPU
5 January 2019Quantum computing to speed up and reduce the cost of software development for the customer
14 January 2021To buy domains with history or create new domain name
2 November 2019Why should you be interested in renting a web hosting with dedicated server?
6 April 2019Forecasts 2020: IT Infrastructure and Support
2 February 2020USB 3.2 doubles the data transfer speed
4 August 20185 myths about the cybersecurity of your site
30 December 2019The first floating DC will be launched in Ireland
13 December 2018Crypto-hacking as a new type of attacks on DC
22 December 2018Data center and its digital transformation
22 August 2018The first DC on the barge again postpones the start of work
16 February 2019Customer requirements for a hybrid cloud
25 July 2018

How to become LIR in 7 days
There is an Internet infrastructure that includes switches, routers, which require a fairly large number of ..
How to avoid mistakes when choosing a hosting
Everyone says that they learn from mistakes, but sometimes these mistakes can lead to very large losses. The..

Chinese manufacturer Loongson will enter the market ..
At the end of September, at the 2018 Xi'an Netcom Military-Civilian Integration Forum conference, where the ..

4 virtualization trends in 2019
According to MarketsandMarket, the virtualization market will grow over the next 5 years. As the main driver..